| .gitignore | ||
| browser-proxy-settings.png | ||
| customgeo.dat | ||
| ex.sh | ||
| LICENSE | ||
| README.md | ||
| template_config_client.jsonc | ||
| template_config_server.jsonc | ||
easy-xray
Script for Linux which makes XRay installation and configuration easy
(todo) Readme in Russian
(todo) Readme in Chinese
XRay (aka ProjectX) is a frontier solution to surpass the internet censorship. It can work as a server and as a client allowing to guide traffic through a VPS outside the region of censorship. XRay configuration can be confusing for a newcomer, so, here is a script which helps to
- install/upgrade/remove XRay and geodata
- generate credentials and server/client configs
- add/delete users to the configs
First, make the script ex.sh executable, then run a desired command with it. Use ./ex.sh help to see the list of all available commands
and ./ex.sh install to start interactive prompt which installs and configures XRay.
$ chmod +x ex.sh
$ ./ex.sh help
$ sudo ./ex.sh install
Prerequisites
For manipulations with configs, jq is needed, it can be found in repositories of almost all popular Linux distributions.
How it works
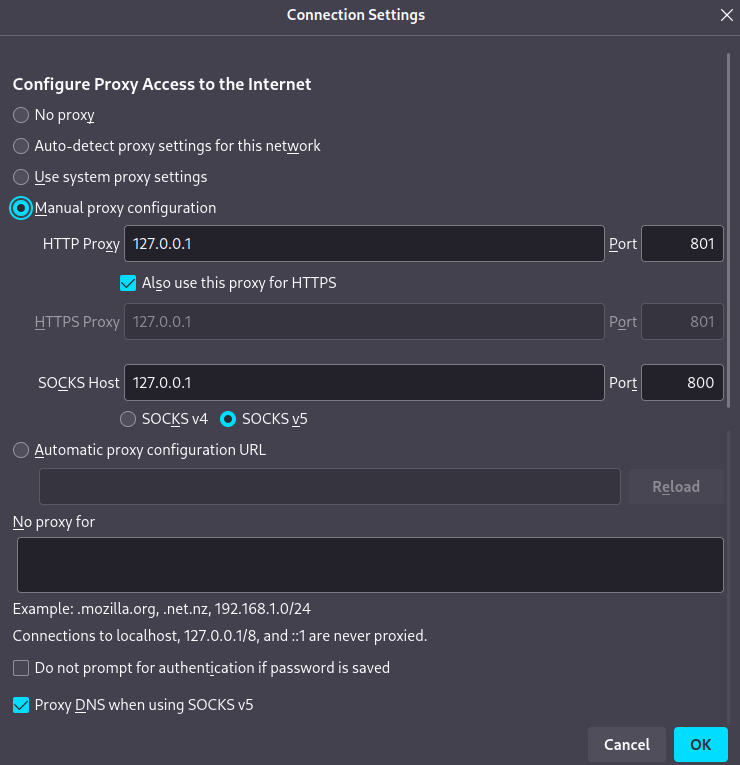
With current configs, XRay creates a tunnel between the client (your laptop, phone etc.) and the server (your VPS). The tunnel uses VLESS Reality protocol that obfuscates traffic and in our case imitates grpc. For the censor the tunnel looks like a usual connection to a site. The server responds to https requests as some popular site thus it is not suspicious for an active probing. On the client side XRay creates http/https and socks proxies which can be used by your Telegram or web browser like this:
Note that there is no additional encryption layer in VLESS; using it you rely on the encryption that the browser (Telegram app etc.) makes. Note also that for current client config, traffic to .cn, .ru, .by and .ir sites goes directly from the client, see here for details. This makes your server much less attention-grabbing and suspicious, but your connection less anonymous.
Other clients
For Windows, MacOS or Android you can try Nekobox, v2rayNG or ? (TODO): tests and config generation for them.
Futher reading
Template configs contain comments and links and are good start to find another interesting Xray configuration options.
Acknowledgements
This article (in Russian) helped me to install XRay for the first time.
XRay config reference is brilliant and helped me much.
Configs for gRPC and XTLS on that the template configs are based.